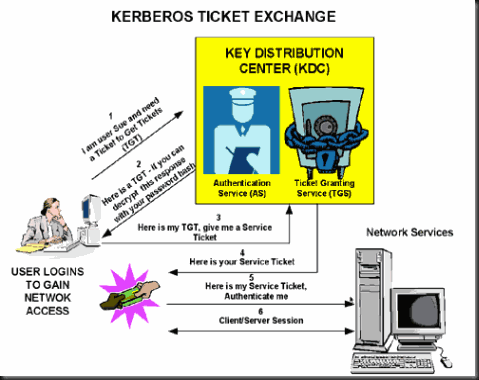
Finally going to start setup Sharepoint2010 ![]() , need to refresh some memory about kerberos. just share the diagram for basic understand.
, need to refresh some memory about kerberos. just share the diagram for basic understand.
information copy from Microsoft:
Typically there are three main reasons to use the Kerberos protocol:
1. Delegation of client credentials — The Kerberos protocol allows a client's identity to be impersonated by a service to allow the impersonating service to pass that identity to other network services on the client's behalf. NTLM does not allow this delegation. (This limitation NTLM is called the "double-hop rule"). Claims authentication, like Kerberos authentication, can be used to delegate client credentials but requires the back-end application to be claims-aware.
2. Security — Features such as AES encryption, mutual authentication, support for data integrity and data privacy, just to name a few, make the Kerberos protocol more secure than its NTLM counterpart.
3. Potentially better performance — Kerberos authentication requires less traffic to the domain controllers compared with NTLM (depending on PAC verification, see Microsoft Open Specification Support Team Blog: Understanding Microsoft Kerberos PAC Validation). If PAC verification is disabled or not needed, the service that authenticates the client does not have to make an RPC call to the DC (see: You experience a delay in the user-authentication process when you run a high-volume server program on a domain member in Windows 2000 or Windows Server 2003). Kerberos authentication also requires less traffic between client and server compared with NTLM. Clients can authenticate with web servers in two request/responses vs. the typical three-leg handshake with NTLM. However, this improvement is typically not noticed on low latency networks on a per-transaction basis, but can typically be noticed in overall system throughput. Remember that many environmental factors can affect authentication performance; therefore Kerberos authentication and NTLM should be performance-tested in your own environment before you determine whether one method performs better than the other.
This is an incomplete list of the advantages of using the Kerberos protocol. There are other reasons like mutual authentication, cross platform interoperability, and transitive cross domain trust, to name a few. However, in most cases one typically finds delegation and security to be the primary drivers in adoption of the Kerberos protocol.